This section allows you to view all posts made by this member. Note that you can only see posts made in areas you currently have access to.
16
Directory and Authentication / [SOLVED] File Sharing does not work
« on: March 28, 2019, 10:34:42 pm »
hello, on my domain controller, create a folder for wallpapers. add security policies so that groups only reading and other groups with higher permissions can read and write.
it does not give me permission to read or write.
/etc/samba/smb.conf
/etc/samba/shares.conf
/home/samba/shares/wallpapers
will it be some permission of the folder?
it does not give me permission to read or write.
/etc/samba/smb.conf
Code: [Select]
administrator@servidor:~$ cat /etc/samba/smb.conf
[global]
workgroup = savidoca
realm = SAVIDOCA.COM
netbios name = servidor
server string = Zentyal Server
server role = dc
server role check:inhibit = yes
server services = -dns
server signing = auto
dsdb:schema update allowed = yes
ldap server require strong auth = no
drs:max object sync = 1200
idmap_ldb:use rfc2307 = yes
winbind enum users = yes
winbind enum groups = yes
template shell = /bin/bash
template homedir = /home/%U
rpc server dynamic port range = 49152-65535
interfaces = lo,eth2
bind interfaces only = yes
map to guest = Bad User
log level = 3
log file = /var/log/samba/samba.log
max log size = 100000
include = /etc/samba/shares.conf
[netlogon]
path = /var/lib/samba/sysvol/savidoca.com/scripts
browseable = no
read only = yes
[sysvol]
path = /var/lib/samba/sysvol
read only = no
/etc/samba/shares.conf
Code: [Select]
administrator@servidor:~$ cat /etc/samba/shares.conf
[homes]
comment = Directorios de usuario
path = /home/%S
read only = no
browseable = no
create mask = 0611
directory mask = 0711
vfs objects = acl_xattr full_audit
full_audit:success = connect opendir disconnect unlink mkdir rmdir open rename
full_audit:failure = connect opendir disconnect unlink mkdir rmdir open rename
# Shares
[wallpapers]
comment = fondos de pantalla
path = /home/samba/shares/wallpapers
browseable = yes
force create mode = 0660
force directory mode = 0660
valid users = @"cybers", @"vendedores", @"gerentes", @"tech"
read list = @"cybers", @"vendedores"
write list = @"gerentes", @"tech"
admin users =
vfs objects = acl_xattr full_audit
full_audit:failure = connect opendir disconnect unlink mkdir rmdir open rename
/home/samba/shares/wallpapers
Code: [Select]
administrator@servidor:~$ ls -la /home/samba/shares
total 16
drwxrwx---+ 3 root SAVIDOCA\domain users 4096 mar 25 11:15 .
drwxrwx---+ 4 root SAVIDOCA\domain users 4096 mar 2 12:51 ..
drwxrwx---+ 2 administrator adm 4096 mar 25 11:15 wallpapers
administrator@servidor:~$ ls -la /home/samba/shares/wallpapers
total 12
drwxrwx---+ 2 administrator adm 4096 mar 25 11:15 .
drwxrwx---+ 3 root SAVIDOCA\domain users 4096 mar 25 11:15 ..
Code: [Select]
administrator@servidor:~$ getfacl /home/samba/shares/wallpapers
getfacl: Removing leading '/' from absolute path names
# file: home/samba/shares/wallpapers
# owner: administrator
# group: adm
user::rwx
user:administrator:rwx
group::rwx
group:adm:rwx
group:SAVIDOCA\134domain\040admins:rwx
mask::rwx
other::---
default:user::rwx
default:user:administrator:rwx
default:group::rwx
default:group:adm:rwx
default:group:SAVIDOCA\134domain\040admins:rwx
default:mask::rwx
default:other::---
will it be some permission of the folder?
17
Directory and Authentication / [Help] Domain controller, ports exposed to the Internet?
« on: March 18, 2019, 08:49:17 pm »
Greetings to Zentyal team.
I find the following doubt.
I have Zentyal Server 6.0 with the modules: domain controller, dns, network, dhcp, firewall, IPS, authority certificate, ftp, ntp and registry.
But the domain controller is not a gateway, I use another UTM solution as a firewall for my network.
my domain controller is "* .com" and I wanted to know what port should be exposed to the Internet?
I find the following doubt.
I have Zentyal Server 6.0 with the modules: domain controller, dns, network, dhcp, firewall, IPS, authority certificate, ftp, ntp and registry.
But the domain controller is not a gateway, I use another UTM solution as a firewall for my network.
my domain controller is "* .com" and I wanted to know what port should be exposed to the Internet?
Code: [Select]
tcp 0 0 192.168.1.2:135 0.0.0.0:* LISTEN 3269/samba
tcp 0 0 127.0.1.1:135 0.0.0.0:* LISTEN 3269/samba
tcp 0 0 127.0.0.1:135 0.0.0.0:* LISTEN 3269/samba
tcp 0 0 127.0.0.1:139 0.0.0.0:* LISTEN 3273/smbd
tcp 0 0 127.0.1.1:139 0.0.0.0:* LISTEN 3273/smbd
tcp 0 0 192.168.1.2:139 0.0.0.0:* LISTEN 3273/smbd
tcp 0 0 192.168.1.2:464 0.0.0.0:* LISTEN 3276/samba
tcp 0 0 127.0.1.1:464 0.0.0.0:* LISTEN 3276/samba
tcp 0 0 127.0.0.1:464 0.0.0.0:* LISTEN 3276/samba
tcp 0 0 172.16.251.1:53 0.0.0.0:* LISTEN 2569/named
tcp 0 0 172.16.14.1:53 0.0.0.0:* LISTEN 2569/named
tcp 0 0 192.168.1.2:53 0.0.0.0:* LISTEN 2569/named
tcp 0 0 201.210.227.42:53 0.0.0.0:* LISTEN 2569/named
tcp 0 0 127.0.1.1:53 0.0.0.0:* LISTEN 2569/named
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN 2569/named
tcp 0 0 192.168.1.2:88 0.0.0.0:* LISTEN 3276/samba
tcp 0 0 127.0.1.1:88 0.0.0.0:* LISTEN 3276/samba
tcp 0 0 127.0.0.1:88 0.0.0.0:* LISTEN 3276/samba
tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN 2569/named
tcp 0 0 192.168.1.2:636 0.0.0.0:* LISTEN 3274/samba
tcp 0 0 127.0.1.1:636 0.0.0.0:* LISTEN 3274/samba
tcp 0 0 127.0.0.1:636 0.0.0.0:* LISTEN 3274/samba
tcp 0 0 127.0.0.1:445 0.0.0.0:* LISTEN 3273/smbd
tcp 0 0 127.0.1.1:445 0.0.0.0:* LISTEN 3273/smbd
tcp 0 0 192.168.1.2:445 0.0.0.0:* LISTEN 3273/smbd
tcp 0 0 192.168.1.2:49152 0.0.0.0:* LISTEN 3269/samba
tcp 0 0 127.0.1.1:49152 0.0.0.0:* LISTEN 3269/samba
tcp 0 0 127.0.0.1:49152 0.0.0.0:* LISTEN 3269/samba
tcp 0 0 192.168.1.2:49153 0.0.0.0:* LISTEN 3269/samba
tcp 0 0 127.0.1.1:49153 0.0.0.0:* LISTEN 3269/samba
tcp 0 0 127.0.0.1:49153 0.0.0.0:* LISTEN 3269/samba
tcp 0 0 192.168.1.2:49154 0.0.0.0:* LISTEN 3269/samba
tcp 0 0 127.0.1.1:49154 0.0.0.0:* LISTEN 3269/samba
tcp 0 0 127.0.0.1:49154 0.0.0.0:* LISTEN 3269/samba
tcp 0 0 192.168.1.2:3268 0.0.0.0:* LISTEN 3274/samba
tcp 0 0 127.0.1.1:3268 0.0.0.0:* LISTEN 3274/samba
tcp 0 0 127.0.0.1:3268 0.0.0.0:* LISTEN 3274/samba
tcp 0 0 192.168.1.2:3269 0.0.0.0:* LISTEN 3274/samba
tcp 0 0 192.168.1.2:389 0.0.0.0:* LISTEN 3274/samba
tcp 0 0 127.0.1.1:3269 0.0.0.0:* LISTEN 3274/samba
tcp 0 0 127.0.1.1:389 0.0.0.0:* LISTEN 3274/samba
tcp 0 0 127.0.0.1:3269 0.0.0.0:* LISTEN 3274/samba
tcp 0 0 127.0.0.1:389 0.0.0.0:* LISTEN 3274/samba
18
Directory and Authentication / Re: Zentyal dns update or retsart issue
« on: January 31, 2019, 08:44:18 pm »
It is strange, it must be that the hostname is not correctly written. try this command to see what the result is.
Code: [Select]
sudo hostname
19
Spanish / Re: [Ayuda] Necesito Mudar el controlador de Dominio Zentyal 5.0 a otro Zentyal 6.0
« on: January 31, 2019, 08:37:36 pm »
Olvide transferir los SYSVOL, perdí las políticas de grupo. 

20
Spanish / Re: [Ayuda] Necesito Mudar el controlador de Dominio Zentyal 5.0 a otro Zentyal 6.0
« on: January 28, 2019, 01:37:42 am »
Bien, ya logre transferir el Controlador de dominio maestro viejo (Servidor Zentyal 5.0), al que estaba de escavo (DC2 Zentyal 6.0) y de nuevo Controlador de Dominio maestro "nuevo" (Servidor Zentyal 6.0), mediante la herramienta RSAT me ayude a convertirlo a maestro.
El problema ahora es como cambio la visualización de esta opción, por que si la cambio a Controlador de Dominio se borran los usuarios, grupos y directivas, a pesar que ya es maestro?
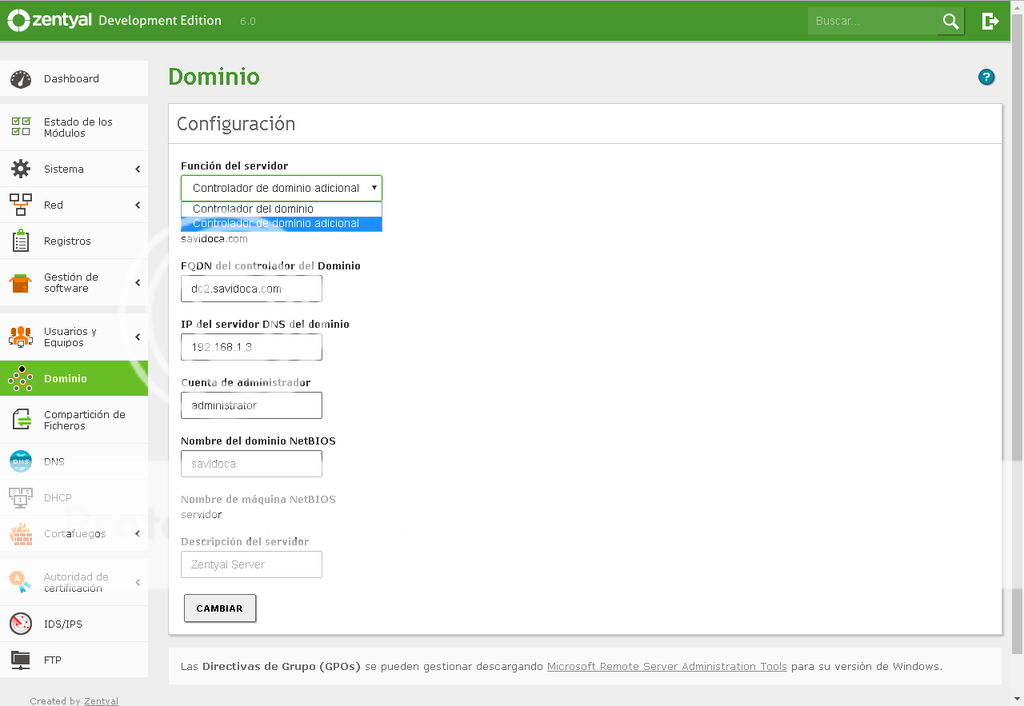
El problema ahora es como cambio la visualización de esta opción, por que si la cambio a Controlador de Dominio se borran los usuarios, grupos y directivas, a pesar que ya es maestro?

21
Spanish / Re: [Ayuda] Necesito Mudar el controlador de Dominio Zentyal 5.0 a otro Zentyal 6.0
« on: January 27, 2019, 11:28:57 pm »
Bueno hasta el momento lo que e investigado.
Tengo un Controlador de Dominio llamado "SERVIDOR" con Zentyal 5.0.
Un Controlador de Dominio adicional al que lo voy a cambiar a principal llamado "DC2" con Zentyal 6.0
Básicamente tengo que transferir los Roles y los Papeles al DC2.
Luego desde el mismo Controlador de Dominio adicional ejecutar el comando para ver quien tiene los roles.
Debe aparece 7 Roles, algo como esto:
Para Transferir los Roles debemos ejecutar el siguiente comando:
Verificamos que todos los roles se transfirieron correctamente:
Para Transferir los Papeles debemos ejecutar el siguiente comando:
Ahora debemos demoler en antiguo controlador de dominio.
entramos desde la consola del antiguo controlador de dominio y escribimos el comando:
Tengo un Controlador de Dominio llamado "SERVIDOR" con Zentyal 5.0.
Un Controlador de Dominio adicional al que lo voy a cambiar a principal llamado "DC2" con Zentyal 6.0
Básicamente tengo que transferir los Roles y los Papeles al DC2.
Luego desde el mismo Controlador de Dominio adicional ejecutar el comando para ver quien tiene los roles.
Code: [Select]
sudo samba-tool fsmo show
Debe aparece 7 Roles, algo como esto:
Code: [Select]
SchemaMasterRole owner: CN=NTDS Settings,CN=SERVIDOR,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=savidoca,DC=com
InfrastructureMasterRole owner: CN=NTDS Settings,CN=SERVIDOR,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=savidoca,DC=com
RidAllocationMasterRole owner: CN=NTDS Settings,CN=SERVIDOR,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=savidoca,DC=com
PdcEmulationMasterRole owner: CN=NTDS Settings,CN=SERVIDOR,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=savidoca,DC=com
DomainNamingMasterRole owner: CN=NTDS Settings,CN=SERVIDOR,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=savidoca,DC=com
DomainDnsZonesMasterRole owner: CN=NTDS Settings,CN=SERVIDOR,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=savidoca,DC=com
ForestDnsZonesMasterRole owner: CN=NTDS Settings,CN=SERVIDOR,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=savidoca,DC=com
Para Transferir los Roles debemos ejecutar el siguiente comando:
Code: [Select]
sudo samba-tool fsmo transfer --role=all -U administrator
Verificamos que todos los roles se transfirieron correctamente:
Code: [Select]
sudo samba-tool fsmo show
SchemaMasterRole owner: CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=savidoca,DC=com
InfrastructureMasterRole owner: CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=savidoca,DC=com
RidAllocationMasterRole owner: CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=savidoca,DC=com
PdcEmulationMasterRole owner: CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=savidoca,DC=com
DomainNamingMasterRole owner: CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=savidoca,DC=com
DomainDnsZonesMasterRole owner: CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=savidoca,DC=com
ForestDnsZonesMasterRole owner: CN=NTDS Settings,CN=DC2,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=savidoca,DC=com
Para Transferir los Papeles debemos ejecutar el siguiente comando:
Code: [Select]
sudo samba-tool fsmo seize --role=all -U administrator
Code: [Select]
Attempting transfer...
This DC already has the 'rid' FSMO role
Transfer successful, not seizing role
Attempting transfer...
This DC already has the 'pdc' FSMO role
Transfer successful, not seizing role
Attempting transfer...
This DC already has the 'naming' FSMO role
Transfer successful, not seizing role
Attempting transfer...
This DC already has the 'infrastructure' FSMO role
Transfer successful, not seizing role
Attempting transfer...
This DC already has the 'schema' FSMO role
Transfer successful, not seizing role
Attempting transfer...
This DC already has the 'domaindns' FSMO role
Transfer successful, not seizing role
Attempting transfer...
This DC already has the 'forestdns' FSMO role
Transfer successful, not seizing role
Ahora debemos demoler en antiguo controlador de dominio.
entramos desde la consola del antiguo controlador de dominio y escribimos el comando:
Code: [Select]
sudo samba-tool domain demote -U administrator
22
Directory and Authentication / Re: Zentyal dns update or retsart issue
« on: January 27, 2019, 10:33:49 pm »
Enter this command via console or via SSH:
where ${hostname} you replace them with your current hostname. example: DC1
"dns-DC1"
Code: [Select]
sudo samba-tool group addmembers DnsAdmins dns-${hostname}
where ${hostname} you replace them with your current hostname. example: DC1
"dns-DC1"
23
Spanish / [Ayuda] Necesito Mudar el controlador de Dominio Zentyal 5.0 a otro Zentyal 6.0
« on: January 27, 2019, 09:29:18 pm »
Hola Buenas Tardes.
Necesito Mudar el Controlador de Dominio Directorio Activo de Zentyal 5.0 a otro Servidor Zentyal 6.0.
Alguien sabe como es el procedimiento?
Necesito Mudar el Controlador de Dominio Directorio Activo de Zentyal 5.0 a otro Servidor Zentyal 6.0.
Alguien sabe como es el procedimiento?
24
Directory and Authentication / Re: Problems installing any graphical interface after installing AD-DC module.
« on: January 26, 2019, 10:04:22 pm »
Apparently nobody understands me, when I install gnome-desktop on ubuntu server, previously installed the zentyal package without the zentyal-samba module.
you can start session without problems in graphic environment.
After installing the zentyal-samba module, it is no longer possible to log in to the graphical environment.
all because the zentyal-samba module modifies the PAM Authentication files.
/etc/pam.d/common-account
When ubuntu-desktop is installed:
/etc/pam.d/common-auth
When ubuntu-desktop is installed:
/etc/pam.d/common-password
When ubuntu-desktop is installed:
/etc/pam.d/common-session
When ubuntu-desktop is installed:
/etc/pam.d/common-session-noninteractive
When ubuntu-desktop is installed:
the part that I do not understand because when I install zentyal server by packages, the graphic environment "zenbuntu-desktop" or "ubuntu-desktop" on ubuntu server does not allow login either.
But installing zentyal server from the iso with graphical interface, has no problems.
I want to try to manually correct this problem, modifying the template that is this file:
/usr/share/zentyal/stubs/samba/acc-zentyal.mas
but I have no idea how to do it.
you can start session without problems in graphic environment.
After installing the zentyal-samba module, it is no longer possible to log in to the graphical environment.
all because the zentyal-samba module modifies the PAM Authentication files.
/etc/pam.d/common-account
When ubuntu-desktop is installed:
Code: [Select]
account [success=1 new_authtok_reqd=done default=ignore] pam_unix.so
account requisite pam_deny.so
account required pam_permit.so
After installing zentyal-samba:Code: [Select]
account [success=1 new_authtok_reqd=done default=ignore] pam_unix.so
account requisite pam_deny.so
account required pam_permit.so
account sufficient pam_localuser.so
Installing zentyal server from the ISO with graphic interface (zenbuntu-desktop):Code: [Select]
account [success=1 new_authtok_reqd=done default=ignore] pam_unix.so
account requisite pam_deny.so
account required pam_permit.so
account sufficient pam_localuser.so
/etc/pam.d/common-auth
When ubuntu-desktop is installed:
Code: [Select]
auth [success=1 default=ignore] pam_unix.so nullok_secure
auth requisite pam_deny.so
auth required pam_permit.so
auth optional pam_cap.so
After installing zentyal-samba:Code: [Select]
auth [success=1 default=ignore] pam_unix.so nullok_secure
auth requisite pam_deny.so
auth required pam_permit.so
auth optional pam_cap.so
Installing zentyal server from the ISO with graphic interface (zenbuntu-desktop):Code: [Select]
auth [success=1 default=ignore] pam_unix.so nullok_secure
auth requisite pam_deny.so
auth required pam_permit.so
auth optional pam_cap.so
/etc/pam.d/common-password
When ubuntu-desktop is installed:
Code: [Select]
password [success=1 default=ignore] pam_unix.so obscure sha512
password requisite pam_deny.so
password required pam_permit.so
password optional pam_gnome_keyring.so
After installing zentyal-samba:Code: [Select]
password requisite pam_pwquality.so retry=3
password [success=2 default=ignore] pam_unix.so obscure use_authtok try_first_pass sha512
password requisite pam_deny.so
password required pam_permit.so
Installing zentyal server from the ISO with graphic interface (zenbuntu-desktop):Code: [Select]
password requisite pam_pwquality.so retry=3
password [success=2 default=ignore] pam_unix.so obscure use_authtok try_first_pass sha512
password requisite pam_deny.so
password required pam_permit.so
/etc/pam.d/common-session
When ubuntu-desktop is installed:
Code: [Select]
session [default=1] pam_permit.so
session requisite pam_deny.so
session required pam_permit.so
session optional pam_umask.so
session required pam_unix.so
session optional pam_systemd.so
After installing zentyal-samba:Code: [Select]
session [default=1] pam_permit.so
session requisite pam_deny.so
session required pam_permit.so
session optional pam_umask.so
session required pam_unix.so
session required pam_mkhomedir.so skel=/etc/skel/ umask=0077
Installing zentyal server from the ISO with graphic interface (zenbuntu-desktop):Code: [Select]
session [default=1] pam_permit.so
session requisite pam_deny.so
session required pam_permit.so
session optional pam_umask.so
session required pam_unix.so
session required pam_mkhomedir.so skel=/etc/skel/ umask=0077
/etc/pam.d/common-session-noninteractive
When ubuntu-desktop is installed:
Code: [Select]
session [default=1] pam_permit.so
session requisite pam_deny.so
session required pam_permit.so
session optional pam_umask.so
session required pam_unix.so
After installing zentyal-samba:Code: [Select]
session [default=1] pam_permit.so
session requisite pam_deny.so
session required pam_permit.so
session optional pam_umask.so
session required pam_unix.so
session optional pam_winbind.so
Installing zentyal server from the ISO with graphic interface (zenbuntu-desktop):Code: [Select]
session [default=1] pam_permit.so
session requisite pam_deny.so
session required pam_permit.so
session optional pam_umask.so
session required pam_unix.so
session optional pam_winbind.so
the part that I do not understand because when I install zentyal server by packages, the graphic environment "zenbuntu-desktop" or "ubuntu-desktop" on ubuntu server does not allow login either.
But installing zentyal server from the iso with graphical interface, has no problems.
I want to try to manually correct this problem, modifying the template that is this file:
/usr/share/zentyal/stubs/samba/acc-zentyal.mas
but I have no idea how to do it.
25
Directory and Authentication / Problems installing any graphical interface after installing AD-DC module.
« on: January 21, 2019, 06:23:50 am »
Hello to the zentyal team and its users.
I have several months trying to find the solution to this problem, when installing the graphical interface of zenbuntu-desktop or the same one of ubuntu-desktop. When the screen is locked in a login cycle when I try to enter my desktop. When I log in, the screen turns black and soon after the login screen reappears.
I took the job of doing several tests until I found the problem, modified the following files.
After installing the module: Active Directory Domain Controller.
He modifies the files:
/etc/pam.d/common-account
/etc/pam.d/common-auth
/etc/pam.d/common-password
/etc/pam.d/common-session
/etc/pam.d/common-session-noninteractive
I have several months trying to find the solution to this problem, when installing the graphical interface of zenbuntu-desktop or the same one of ubuntu-desktop. When the screen is locked in a login cycle when I try to enter my desktop. When I log in, the screen turns black and soon after the login screen reappears.
I took the job of doing several tests until I found the problem, modified the following files.
After installing the module: Active Directory Domain Controller.
He modifies the files:
/etc/pam.d/common-account
/etc/pam.d/common-auth
/etc/pam.d/common-password
/etc/pam.d/common-session
/etc/pam.d/common-session-noninteractive
Code: [Select]
administrator@servidor:~$ diff /etc/pam.d/common-account.backup /etc/pam.d/common-account
16,19c16,20
< # here are the per-package modules (the "Primary" block)
< account [success=1 new_authtok_reqd=done default=ignore] pam_unix.so
< # here's the fallback if no module succeeds
< account requisite pam_deny.so
---
> # pre_auth-client-config # # here are the per-package modules (the "Primary" block)
> # pre_auth-client-config # account [success=2 new_authtok_reqd=done default=ignore] pam_unix.so
> # pre_auth-client-config # account [success=1 new_authtok_reqd=done default=ignore] pam_winbind.so
> # pre_auth-client-config # # here's the fallback if no module succeeds
> # pre_auth-client-config # account requisite pam_deny.so
23,25c24,30
< account required pam_permit.so
< # and here are more per-package modules (the "Additional" block)
< # end of pam-auth-update config
---
> # pre_auth-client-config # account required pam_permit.so
> # pre_auth-client-config # # and here are more per-package modules (the "Additional" block)
> # pre_auth-client-config # # end of pam-auth-update config
> account [success=1 new_authtok_reqd=done default=ignore] pam_unix.so
> account requisite pam_deny.so
> account required pam_permit.so
> account sufficient pam_localuser.so
Code: [Select]
administrator@servidor:~$ diff /etc/pam.d/common-auth.backup /etc/pam.d/common-auth
16,19c16,20
< # here are the per-package modules (the "Primary" block)
< auth [success=1 default=ignore] pam_unix.so nullok_secure
< # here's the fallback if no module succeeds
< auth requisite pam_deny.so
---
> # pre_auth-client-config # # here are the per-package modules (the "Primary" block)
> # pre_auth-client-config # auth [success=2 default=ignore] pam_unix.so nullok_secure
> # pre_auth-client-config # auth [success=1 default=ignore] pam_winbind.so krb5_auth krb5_ccache_type=FILE cached_login try_first_pass
> # pre_auth-client-config # # here's the fallback if no module succeeds
> # pre_auth-client-config # auth requisite pam_deny.so
23,26c24,31
< auth required pam_permit.so
< # and here are more per-package modules (the "Additional" block)
< auth optional pam_cap.so
< # end of pam-auth-update config
---
> # pre_auth-client-config # auth required pam_permit.so
> # pre_auth-client-config # # and here are more per-package modules (the "Additional" block)
> # pre_auth-client-config # auth optional pam_cap.so
> # pre_auth-client-config # # end of pam-auth-update config
> auth [success=1 default=ignore] pam_unix.so nullok_secure
> auth requisite pam_deny.so
> auth required pam_permit.so
> auth optional pam_cap.so
Code: [Select]
administrator@servidor:~$ diff /etc/pam.d/common-password.backup /etc/pam.d/common-password
24,27c24,29
< # here are the per-package modules (the "Primary" block)
< password [success=1 default=ignore] pam_unix.so obscure sha512
< # here's the fallback if no module succeeds
< password requisite pam_deny.so
---
> # pre_auth-client-config # # here are the per-package modules (the "Primary" block)
> # pre_auth-client-config # password requisite pam_pwquality.so retry=3
> # pre_auth-client-config # password [success=2 default=ignore] pam_unix.so obscure use_authtok try_first_pass sha512
> # pre_auth-client-config # password [success=1 default=ignore] pam_winbind.so use_authtok try_first_pass
> # pre_auth-client-config # # here's the fallback if no module succeeds
> # pre_auth-client-config # password requisite pam_deny.so
31,34c33,40
< password required pam_permit.so
< # and here are more per-package modules (the "Additional" block)
< password optional pam_gnome_keyring.so
< # end of pam-auth-update config
---
> # pre_auth-client-config # password required pam_permit.so
> # pre_auth-client-config # # and here are more per-package modules (the "Additional" block)
> # pre_auth-client-config # password optional pam_gnome_keyring.so
> # pre_auth-client-config # # end of pam-auth-update config
> password requisite pam_pwquality.so retry=3
> password [success=2 default=ignore] pam_unix.so obscure use_authtok try_first_pass sha512
> password requisite pam_deny.so
> password required pam_permit.so
Code: [Select]
administrator@servidor:~$ diff /etc/pam.d/common-session.backup /etc/pam.d/common-session
15,18c15,18
< # here are the per-package modules (the "Primary" block)
< session [default=1] pam_permit.so
< # here's the fallback if no module succeeds
< session requisite pam_deny.so
---
> # pre_auth-client-config # # here are the per-package modules (the "Primary" block)
> # pre_auth-client-config # session [default=1] pam_permit.so
> # pre_auth-client-config # # here's the fallback if no module succeeds
> # pre_auth-client-config # session requisite pam_deny.so
22c22
< session required pam_permit.so
---
> # pre_auth-client-config # session required pam_permit.so
27,31c27,38
< session optional pam_umask.so
< # and here are more per-package modules (the "Additional" block)
< session required pam_unix.so
< session optional pam_systemd.so
< # end of pam-auth-update config
---
> # pre_auth-client-config # session optional pam_umask.so
> # pre_auth-client-config # # and here are more per-package modules (the "Additional" block)
> # pre_auth-client-config # session required pam_unix.so
> # pre_auth-client-config # session optional pam_winbind.so
> # pre_auth-client-config # session optional pam_systemd.so
> # pre_auth-client-config # # end of pam-auth-update config
> session [default=1] pam_permit.so
> session requisite pam_deny.so
> session required pam_permit.so
> session optional pam_umask.so
> session required pam_unix.so
> session required pam_mkhomedir.so skel=/etc/skel/ umask=0077
Code: [Select]
administrator@servidor:~$ diff /etc/pam.d/common-session-noninteractive.backup /etc/pam.d/common-session-noninteractive
29a30
> session optional pam_winbind.so
26
Spanish / Re: Migrar de un servidor Zentyal a otro sin perder Datos
« on: December 22, 2018, 06:06:48 pm »
Hola yo quiero hacer lo mismo, pero en mi caso hice la instalación de Zentyal Server 6.0 en limpio, pero al instalar la interfaz gráfica del escritorio, no funciona, el login no carga correctamente y no se puede iniciar sesión.
27
Spanish / Re: [AYUDA] HTTP Redirect
« on: December 22, 2018, 06:02:54 pm »
El problema es que cuando reinicias Zentyal, se borrar la configuración manual.
Yo solucione el problema con otro equipo y un firewall UTM comercial.
muchas gracias.
Yo solucione el problema con otro equipo y un firewall UTM comercial.
muchas gracias.
28
Spanish / Re: [Desarrollo] Bash Script Samba-AD-DC Bind9_DLZ Backend
« on: September 22, 2018, 10:36:46 pm »
woao, mas de 200 a visto mi tema y nadie opina nada... 

29
Spanish / [Solucion] Apagones, error initramfs
« on: September 08, 2018, 11:31:16 pm »
Hola, esto me paso ayer, con los constantes apagones. ya que la batería del ups de mi servidor se venció.
Pues al arrancar el sistema operativo de ubuntu bajo zentyal, quedo en el error (initramfs)
Para repararlo se hace el siguiente comando:
sfck /dev/mapper/<hostname>--<LVMgroup-root> -y
como mi disco esta particionado LVM
Mi hostname es: SERVIDOR
Mi grupo LVM es vg_servidor
Mi volumen LVM es donde esta el sistema operativo: root
Espero que sea de ayuda para los que están comenzando.
Pues al arrancar el sistema operativo de ubuntu bajo zentyal, quedo en el error (initramfs)
Para repararlo se hace el siguiente comando:
sfck /dev/mapper/<hostname>--<LVMgroup-root> -y
como mi disco esta particionado LVM
Mi hostname es: SERVIDOR
Mi grupo LVM es vg_servidor
Mi volumen LVM es donde esta el sistema operativo: root
Code: [Select]
sfck /dev/mapper/SERVIDOR--vg_servidor-root -y
reboot
Espero que sea de ayuda para los que están comenzando.
30
Spanish / Re: Sobre GPO plantillas
« on: September 08, 2018, 11:22:15 pm »
hola, es mas o menos tedioso.
Primero tienes que tomar un equipo con Windows 10 v1803 Abril 2018 o el de Agosto que esta por salir, este equipo te va a servir para agregar las políticas que quieres implementar en la empresa, lo conectas al dominio creado, e inicias sesión con la cuenta del dominio "administrator".
Una ves abierta la sesión, debes agregar el idioma Ingles, reiniciar el equipo, ya que la herramienta RSAT de Windows Server 2016 solo funciona en Ingles.
Descarga e Instala RSAT de Windows Server 2016 y se van aplicar varias actualizaciones y reiniciar el equipo.
Luego agregas las plantillas en el mismo equipo asi sea de office, adobe, google, etc.. y se van a sincronizar en zentyal en el directorio de políticas.
Primero tienes que tomar un equipo con Windows 10 v1803 Abril 2018 o el de Agosto que esta por salir, este equipo te va a servir para agregar las políticas que quieres implementar en la empresa, lo conectas al dominio creado, e inicias sesión con la cuenta del dominio "administrator".
Una ves abierta la sesión, debes agregar el idioma Ingles, reiniciar el equipo, ya que la herramienta RSAT de Windows Server 2016 solo funciona en Ingles.
Descarga e Instala RSAT de Windows Server 2016 y se van aplicar varias actualizaciones y reiniciar el equipo.
Luego agregas las plantillas en el mismo equipo asi sea de office, adobe, google, etc.. y se van a sincronizar en zentyal en el directorio de políticas.
